Install and Configure Captive Portal with FreeRADIUS on pfSense
How to install & Configure Captive Portal with FreeRadius with Pfsense Firewall
Table of contents
- What is Captive Portal?
- STEP 1:- Install FreeRADIUS3 Package
- STEP 2:- Create Server certificate
- STEP 3:- Configure FreeRadius Server
- STEP 4:- Configure Captive Portal
What is Captive Portal?
Captive portal is use for authenticated users to grant internet access. Firewall automatically captive portal authentication login page which users must use their credentials to enter the portal. User can use Username/Password or a voucher code.
This setup is commonly used throughout the hospitality industries like Airports, Hotels, Restaurants and corporate environments.
The Captive Portal function in Pfsense securing a network by requiring a username and password via portal access web page.
Pfsense built-in user management, LADP, RADIUS can be used as an authentication server.
In this tutorial I’m using FreeRADIUS2 as an authentication server.
STEP 1:- Install FreeRADIUS3 Package
Navigate to System > Package Manager, Available Packages tab
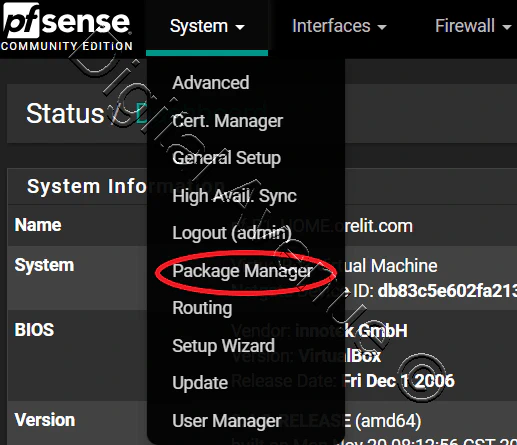
Click
![]() at the end of the row for FreeRADIUS3
at the end of the row for FreeRADIUS3
Confirm the installation
System > Package Manager > Available Packages
[Search Item] = freeradius3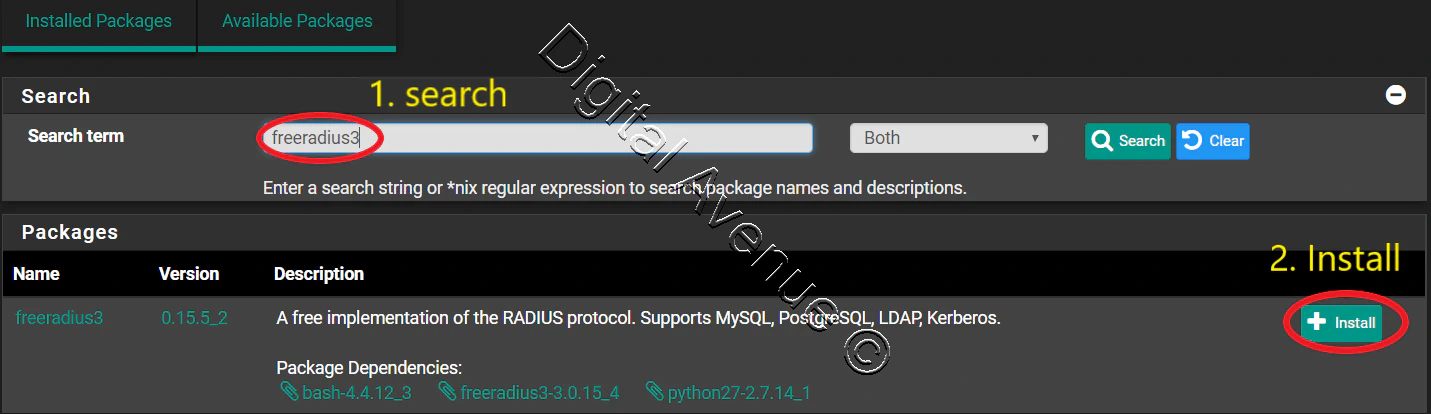
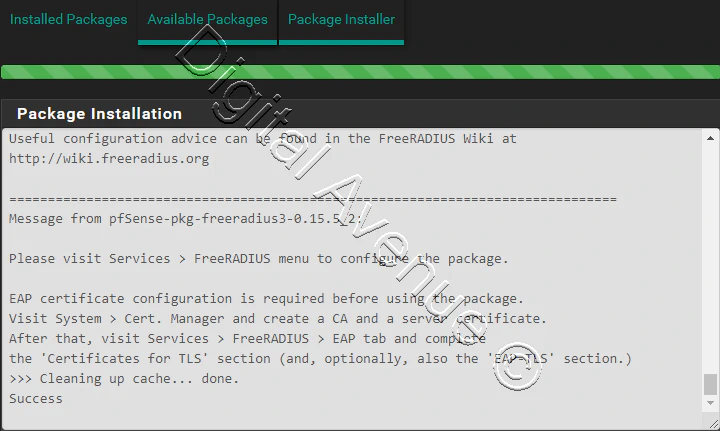
STEP 2:- Create Server certificate
Navigate to System > Cert. Manager
Create a Certificate Authority (CA)
Create a Server Certificate
How to create CA and Server certificate is available at…
STEP 3:- Configure FreeRadius Server
Navigate to System > FreeRadius, EAP Tab > “Certificates for TLS” section
Provide CA and server certificate that we have generated at previous step.
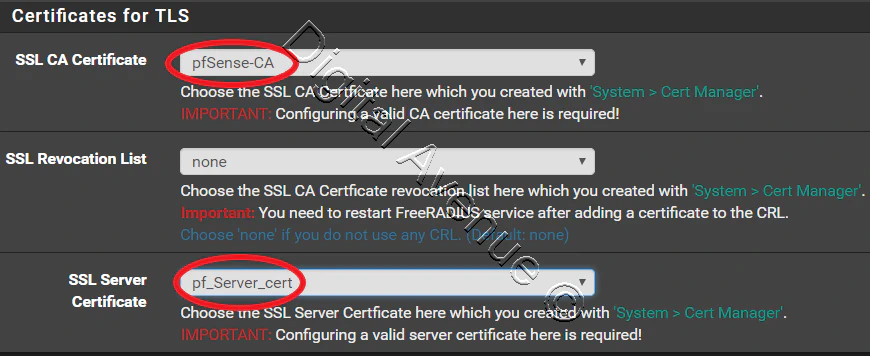
Save the changes.
Add a new interface on which the RADIUS server should listen on.
Navigate to System > Services > FreeRADIUS, Interfaces tab
Click
![]() button
button
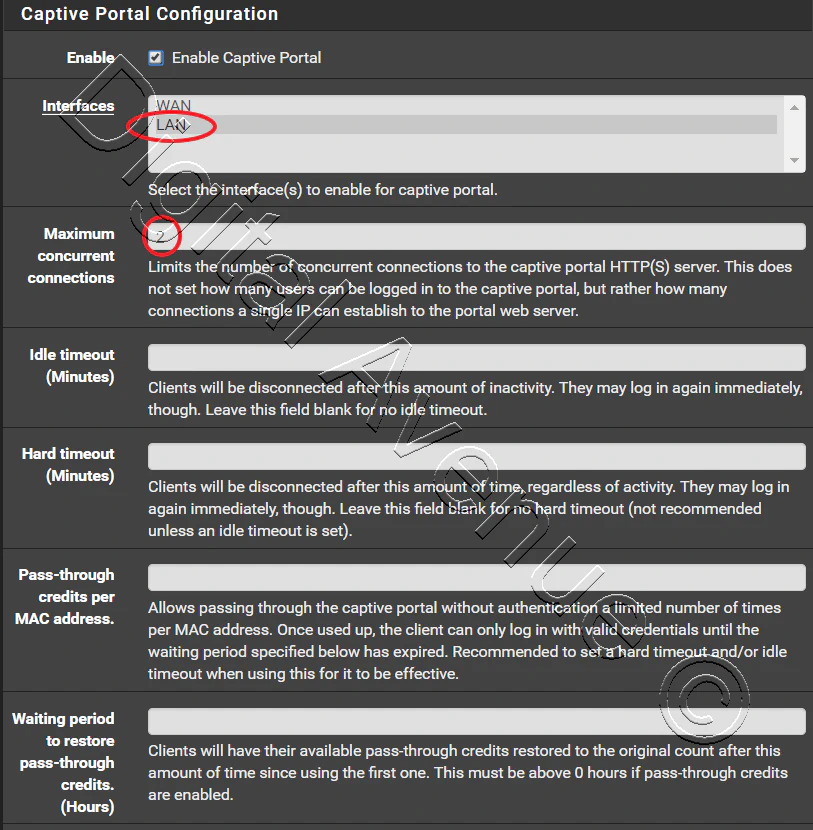
In this case I’m using my LAN interface (192.168.100.1) for RADIUS server to listening on.
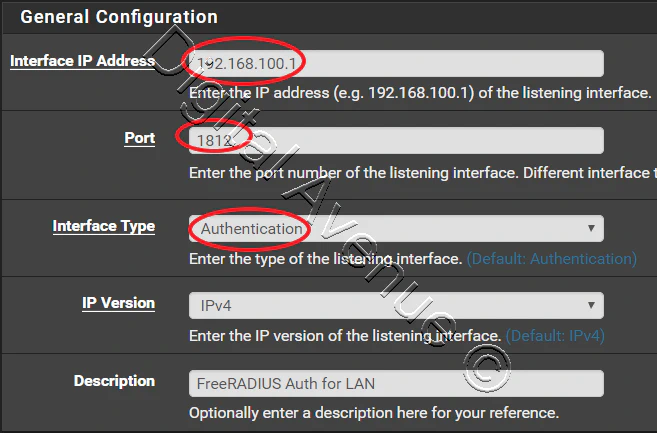
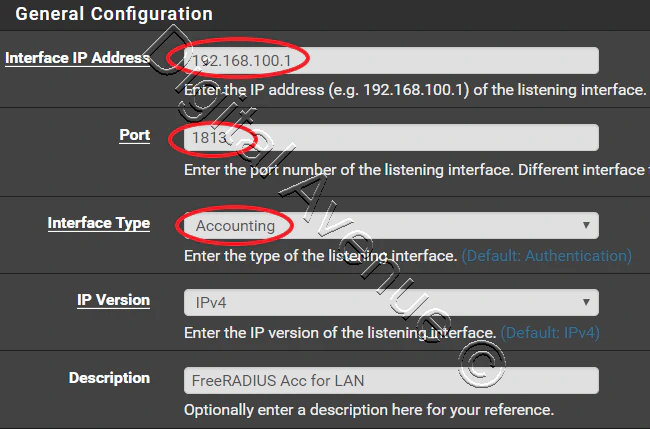
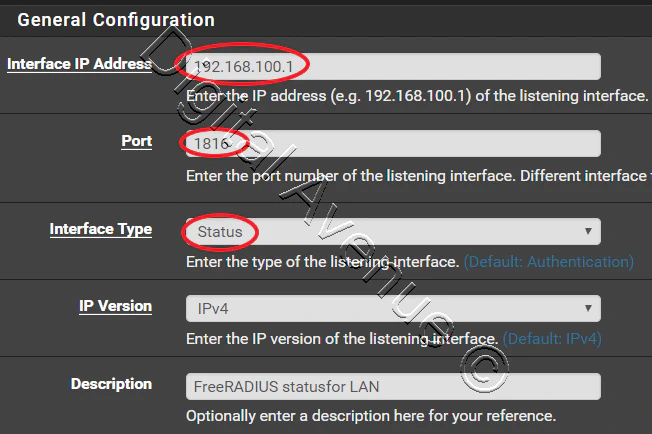
Save and exit.
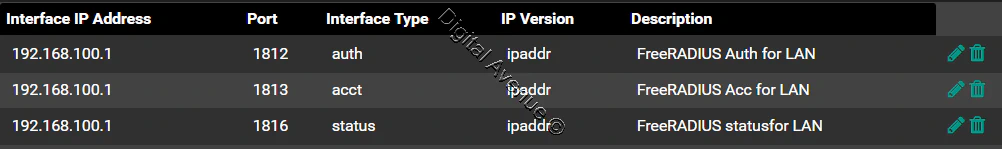
Configure the NAS:
Configure the NAS/client(s) from which the RADIUS server should accept packets.
In this step you need to give the IP address of the device which you want to authenticate from radius server like a firewall, access point, switch and router.
In this step I give my Pfsense box’s IP address because I will use the Pfsense captive portal.
Click “+” button to add the NAS/Clients.
Client IP Address : 192.168.100.1
Client Shortname: captiveportal
Client Shared Secret: 12345
Reset of the settings can be leave default.
https://digitalavenue.dev//img/post-imgs/pfsense_captive_portal/image0010.png does not exist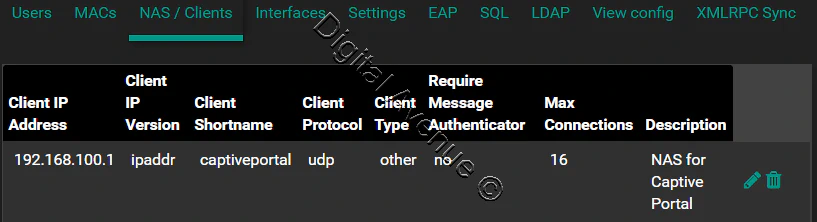
STEP 4:- Configure Captive Portal
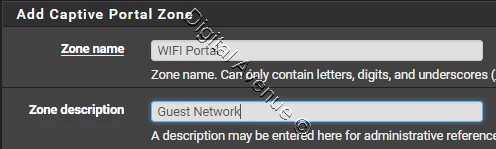
Navigate to Services > Captive Portal
Click “
![]() “ button to add new zone.
“ button to add new zone.

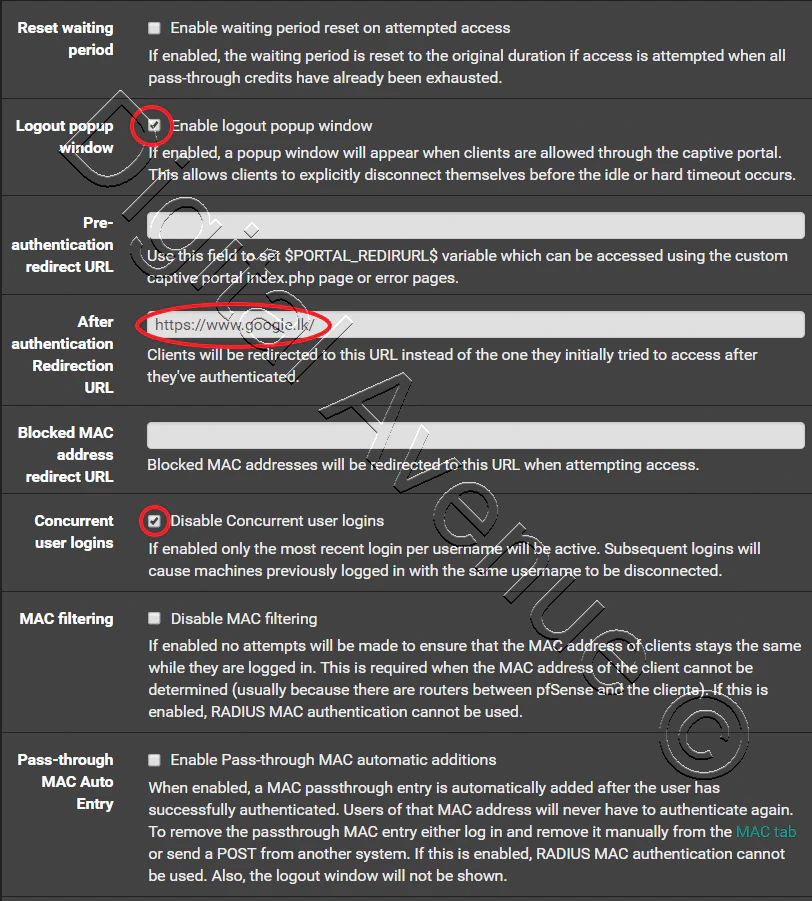
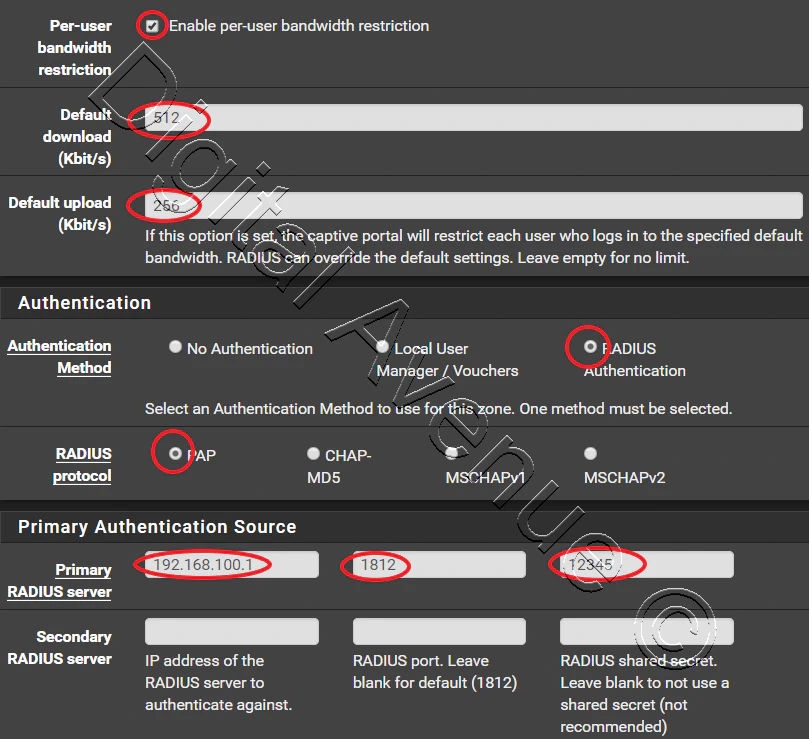
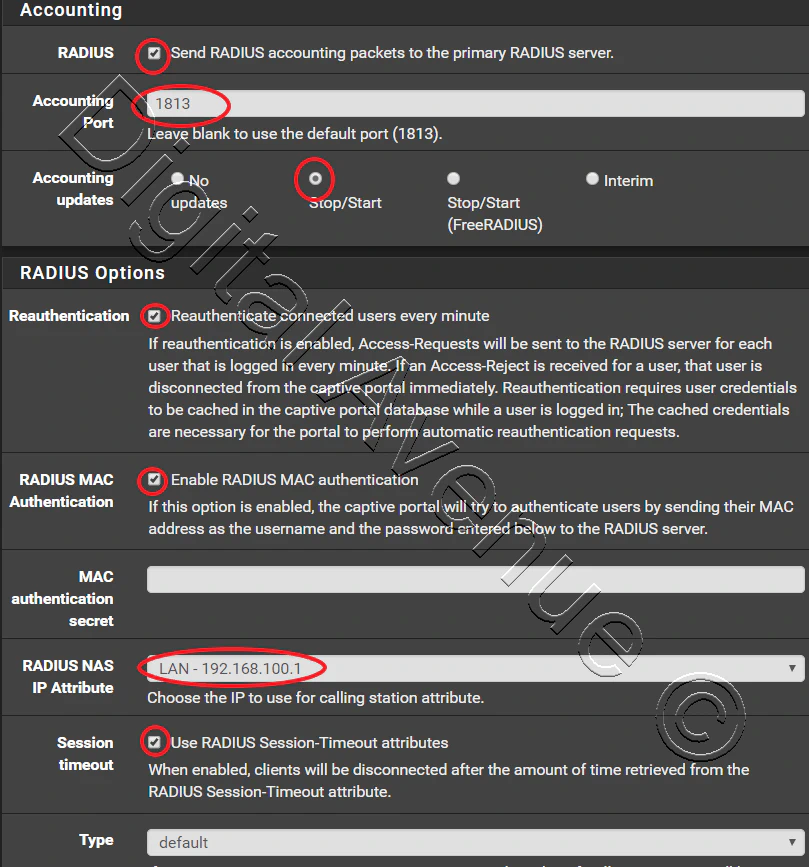
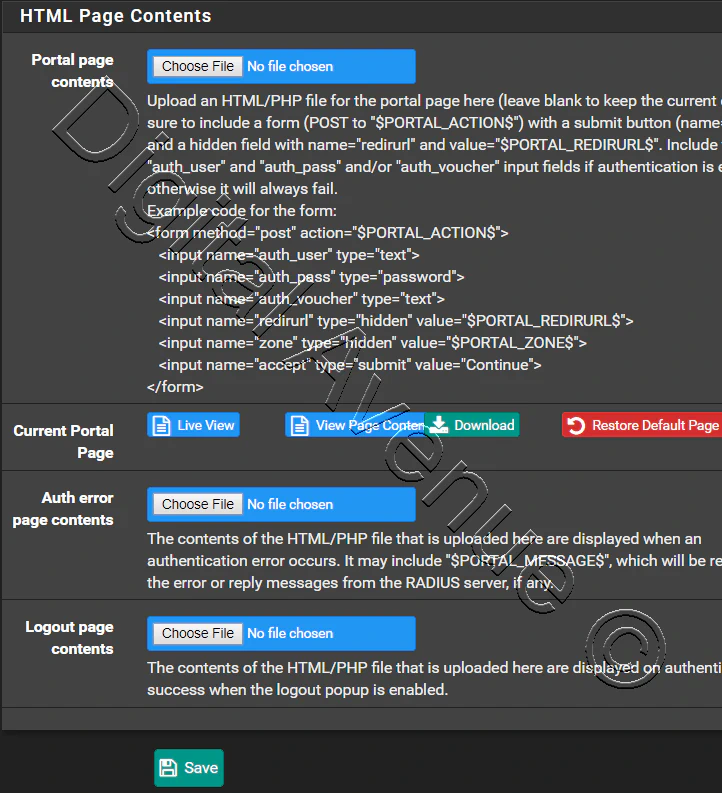
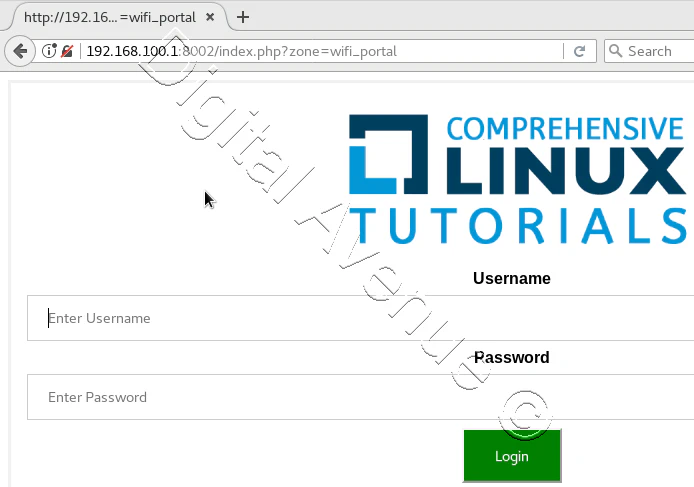
STEP 04:- Create FreeRadius Users
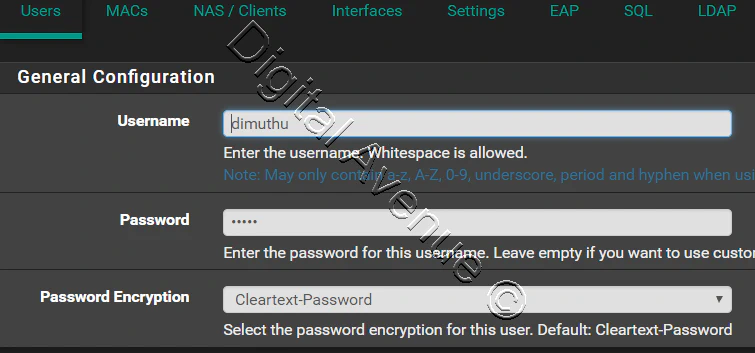
Navigate to Services > FreeRadius, Users tab.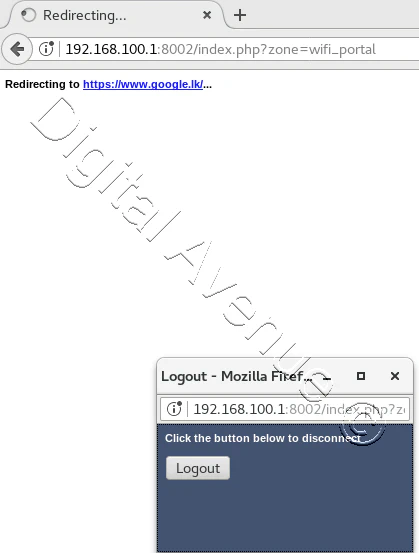
All the other settings can be change upon to your requirements.
STEP 05:- Login to Captive Portal User Account
Deploy Production Grade Kubernetes Cluster on Azure AKS
Introduction This tutorial is intended to demonstrate how to setup your 1st Kubernetes cluster on Azure Kubernetes Services (AKS). This tutorial will cover up all the steps that you need to setup complete AKS cluster.
Getting Started With Docker - Quick Start Guide
Getting Started With Docker - Quick Start Guide Docker Engine Platform as a Service (PaaS) Cloud platform service. Allows you to manage its application and data.
How To Run Microsoft SQL Server On Kubernetes - Azure Kubernetes Service
Prerequisites: Azure CLI https://docs.microsoft.com/en-us/cli/azure/install-azure-cli 1. Run the Azure CLI with the az command. 1.1 Run the login command. az login Login in the browser with the azure account.


